Differences between TCP and UDP
Contents
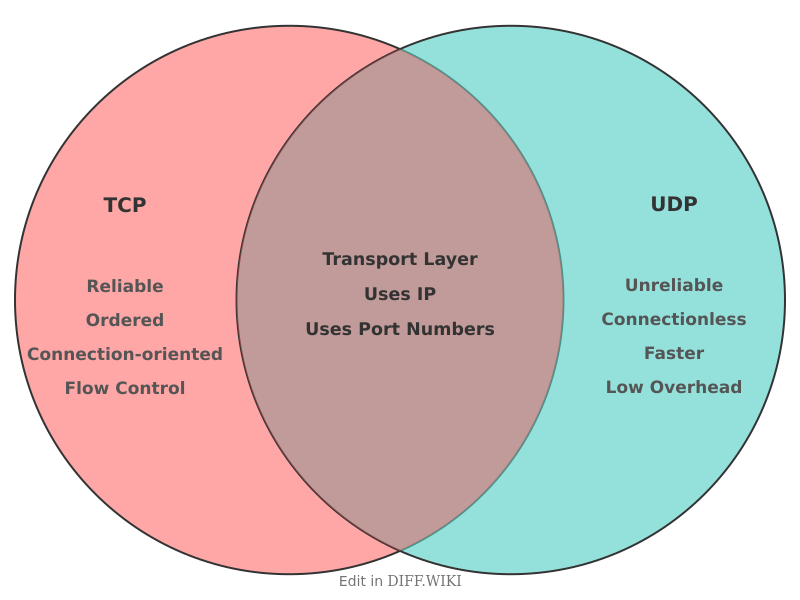
TCP vs. UDP
Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are core protocols of the Internet protocol suite.[1] Both protocols operate at the transport layer to transmit data between applications on hosts communicating over an IP network. However, they are designed with different objectives; TCP prioritizes reliability, while UDP prioritizes speed and low latency.[2][3]
TCP is a connection-oriented protocol that establishes a connection between two devices before sending data.[4] This connection is established through a process known as a three-way handshake (SYN, SYN-ACK, ACK), which ensures that both the sender and receiver are ready to communicate.[5] TCP guarantees that data is delivered in the correct order and without errors by using sequence numbers, acknowledgments, and retransmissions of lost packets. These reliability mechanisms make TCP suitable for applications where data integrity is critical, such as web browsing, email, and file transfers.
UDP, in contrast, is a connectionless protocol. It sends data in packets, called datagrams, without establishing a prior connection or guaranteeing delivery. This "fire-and-forget" approach results in lower overhead and faster transmission speeds because it does not have mechanisms for ordering, error checking, or retransmitting lost packets. Consequently, UDP is well-suited for time-sensitive applications where speed is more important than perfect data integrity, such as live video streaming, online gaming, and Voice over IP (VoIP).
Comparison Table
| Category | Transmission Control Protocol (TCP) | User Datagram Protocol (UDP) |
|---|---|---|
| Connection Type | Connection-oriented | Connectionless[1] |
| Reliability | High reliability with guaranteed packet delivery, order, and error checking | Unreliable; no guarantee of packet delivery or order |
| Speed | Slower, due to reliability mechanisms like handshakes and acknowledgments | Faster, due to lower overhead and no connection setup |
| Header Size | 20 bytes (without options) | 8 bytes |
| Data Ordering | Ensures data is reassembled in the correct order | Does not guarantee the order of packet arrival |
| Error Checking | Extensive error checking and recovery | Basic checksum for data integrity, but no error recovery[1] |
| Flow Control | Manages data flow to prevent overwhelming the receiver[4] | No flow control mechanism |
| Use Cases | Web browsing (HTTP/HTTPS), email (SMTP, IMAP), file transfer (FTP) | Video streaming, online gaming, VoIP, DNS[2] |
TCP Characteristics
TCP's design emphasizes reliable data transfer. It achieves this through several key mechanisms. The protocol is connection-oriented, requiring a three-way handshake to establish a session before any data is sent. This ensures both ends of the communication are ready.
To guarantee that data arrives complete and in the correct sequence, TCP numbers the data segments. The receiving host sends acknowledgments for received segments, and if the sender does not receive an acknowledgment within a certain timeframe, it retransmits the data. This process corrects for packets that may be lost or corrupted during transit. TCP also implements flow control to manage the rate of data transmission, preventing a faster sender from overwhelming a slower receiver.[4]
UDP Characteristics
UDP is designed for speed and efficiency, which it achieves by forgoing the reliability mechanisms found in TCP. As a connectionless protocol, UDP does not perform a handshake to establish a connection before sending data; it simply sends the datagrams to the destination.
This lack of connection setup and the absence of features like sequencing and acknowledgments result in a much lower overhead. The UDP header is significantly smaller than the TCP header, contributing to its efficiency. While UDP includes a checksum to check for data corruption, it does not attempt to recover lost packets.[1] Applications that use UDP must be able to tolerate some level of data loss or implement their own reliability measures.
References
- ↑ 1.0 1.1 1.2 1.3 "wikipedia.org". Retrieved November 30, 2025.
- ↑ 2.0 2.1 "wikipedia.org". Retrieved November 30, 2025.
- ↑ "avast.com". Retrieved November 30, 2025.
- ↑ 4.0 4.1 4.2 "uninets.com". Retrieved November 30, 2025.
- ↑ "ezexplanation.com". Retrieved November 30, 2025.